Single Sign-On (SAML)
Log-in to your Kimai-Cloud with your company credentials
This feature is available for annual PRO subscriptions, check the feature comparison page for more details.
Users of your Kimai-Cloud can authenticate using an identity provider that supports SSO (Single Sign-On) via SAML. You find the configuration after login at: My Kimai-Cloud > SSO Authentication.
Currently, the following providers are supported:
Important to know
- Existing cloud users will be upgraded to SAML logins, after their first SAML login (if identifier matches)
- SAML users cannot log in with password
- Without configured role mapping, every SAML user will only own the
Userrole (even Admins will be downgraded on every login)
Further settings
The SSO configuration includes three settings, which can be de-/activated via toggles (checkboxes):
Activate SSO Login- this toggles the login via SSO buttonActivate regular login with username- this toggles the username/password form (can be deactivated if every user logs in with SSO)Reset assigned user roles during login- if activated user roles will be removed upon login: custom role assignments are only temporary until the next login
Google SAML
Workspace configuration
- Go to https://admin.google.com/ac/apps/unified
- Choose “Add app” followed by “Add custom SAML app”
- Choose your name (e.g. “Kimai-Cloud Live”) and add this image
- Copy & paste the values from the Google Step-by-Step (page 2) guide into your Kimai-Cloud SAML configuration screen:
SSO-URLintoSingle Sign-On URLEntity-IDintoEntity IDCertificateintoX.509 Certificate
- Copy & paste the values from the Kimai-Cloud SAML configuration screen into Google Step-by-Step guide (page 3):
ACS-URLintoACS-URLEntity IDintoEntity-ID- Choose the
Name-ID Format: “X509_SUBJECT” - Select the
Name-ID: “Basic Information > Primary Email”
- On page 4
Attributesyou have to define theUser attributemapping like this (correct case is important, and you need to configure all attributes, even if you do not use them):Basic Information > Primary email→EmailBasic Information > First name→FirstName(optional)Basic Information > Last name→LastName(optional)Employee Details > Employee ID→AccountNumber(optional)Employee Details > Title→Title(optional)
- Back on the overview page: activate the new application for your users
- The last configuration step takes care of the
User rolemapping, which can be defined in two ways:- Using Google Groups (recommended):
- Create Groups for the Kimai roles you want to apply under Directory > Groups
- Apply these groups to your users
- Go back to edit your SAML application and configure the optional group-membership:
- Choose all groups you configured for Kimai and map them to the App-Attribute
Groups
- Choose all groups you configured for Kimai and map them to the App-Attribute
- Using a custom attribute:
- Create a User defined attribute called
SAML Group - Add a field
KimaiRoleas text type with multi-value - Edit your users and apply the values within the new attribute:
- The value
Kimai-Systemmaps to the Kimai roleSystem-Admin - The value
Kimai-Adminmaps to the Kimai roleAdministrator - The value
Kimai-Teamleadmaps to the Kimai roleTeamlead
- The value
- Go back to edit your SAML application and configure one more attribute mapping:
- The Google directory attribute
SAML Group > KimaiRoleto the App-AttributeGroups
- The Google directory attribute
- Create a User defined attribute called
- Using Google Groups (recommended):
You can use other names for your groups, the mapping happens in the next step in your Cloud configuration.
This screenshot is a showcase of the attribute mapping including groups:
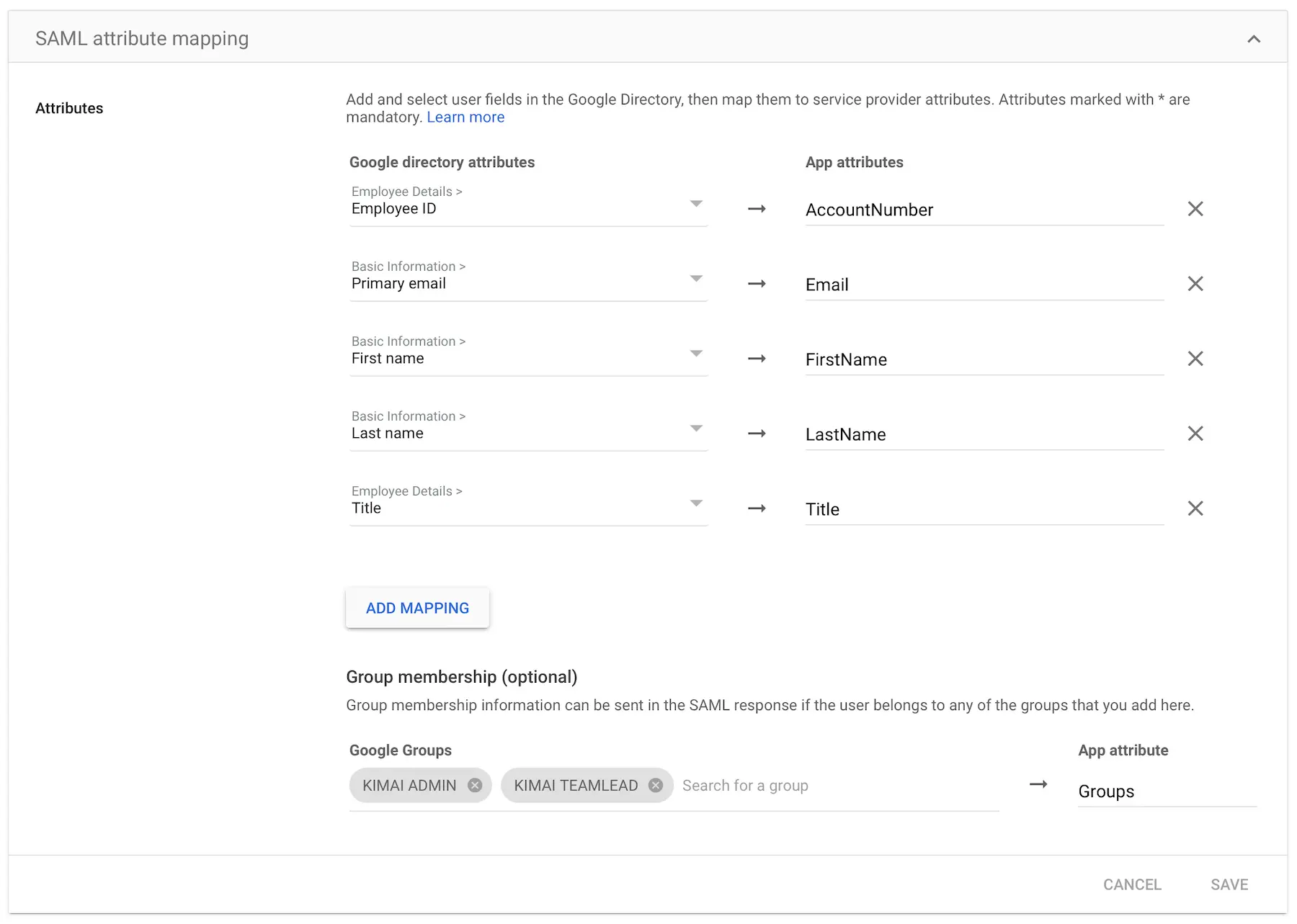
Cloud configuration
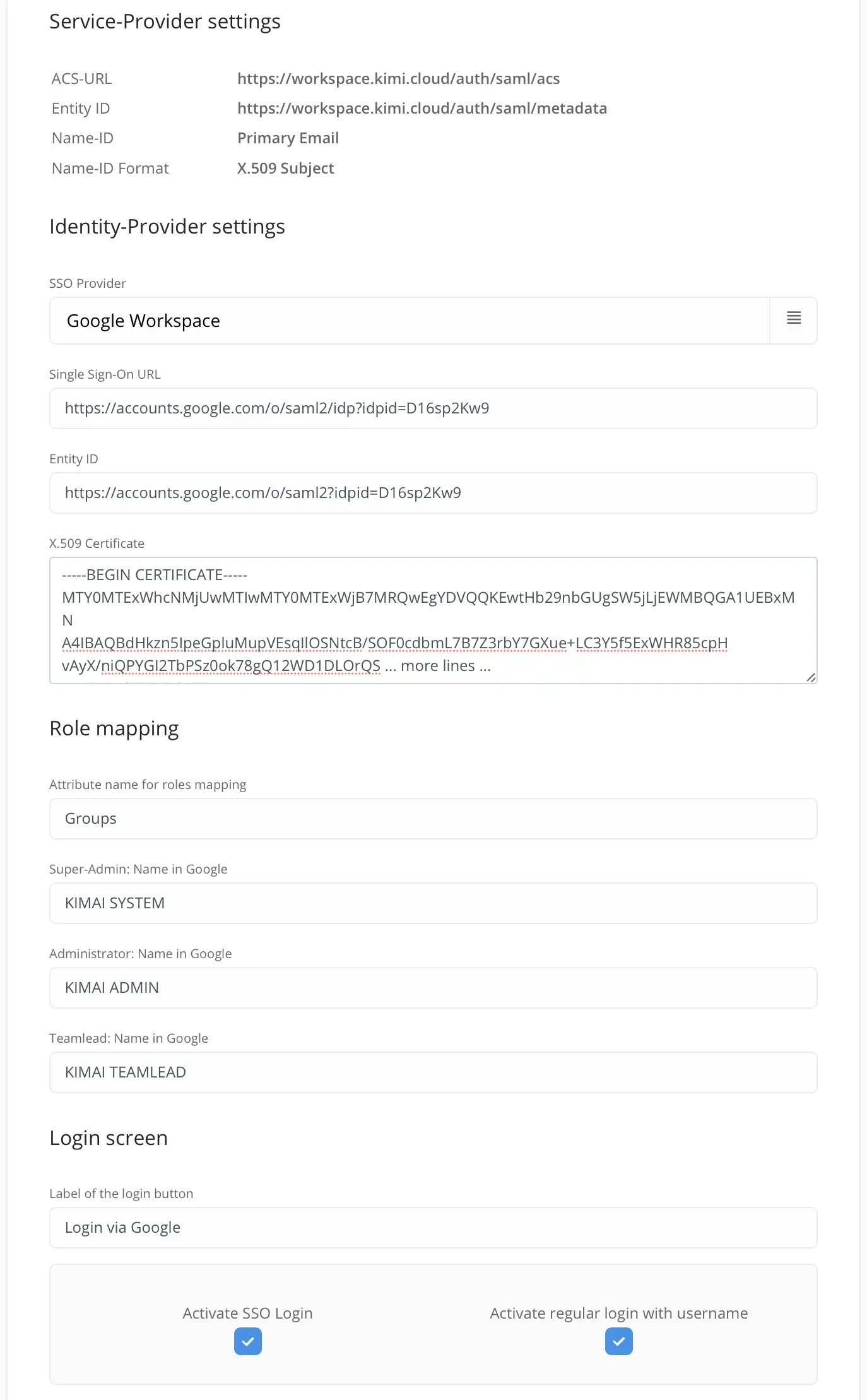
Microsoft SAML
Entra ID (ex. Azure AD) Configuration
- Sign in to the Azure portal.
- Select the Microsoft Entra ID service from the navigation.
- Navigate to Enterprise Applications and then select New application.
- In the “Browse Microsoft Entra Gallery” section, search for Microsoft Entra SAML Toolkit and select it.
- Enter the application name to “Kimai-Cloud”, hit the
Createbutton add wait for the app to be added. - On the “Overview” page select “Assign user and groups” and add all users that should have access to Kimai.
- Back on the “Overview” page select “Set up single sign on” and choose SAML as your choice.
- Edit the Basic SAML Configuration and add the required URLs:
- Replace
foo.kimai.cloudin the following examples with your cloud domain - Identifier (Entity ID):
https://foo.kimai.cloud/auth/saml/metadata - Reply URL (Assertion Consumer Service URL):
https://foo.kimai.cloud/auth/saml/acs - Sign on URL:
https://foo.kimai.cloud/ - Relay State (Optional) - skip this one
- Logout Url (Optional) - skip this one
- Replace
- After saving the URLs: edit the Attributes & Claims and configure required settings (see screenshot below):
- Change
Source attributeof theUnique User Identifier (Name ID)touser.mail - Select
Add a group claimwith the settingsAll groupsand the Source attributeGroup ID - Now you can add optional attributes, which Kimai supports (from the
http://schemas.xmlsoap.org/ws/2005/05/identity/claimsnamespace):- Select
Add new claimwith Name:givenname, Source attribute:user.givenname(optional) - Select
Add new claimwith Name:surname, Source attribute:user.surname(optional) - Select
Add new claimwith Name:displayname, Source attribute:user.displayname(optional) - Select
Add new claimwith Name:employeeid, Source attribute:user.employeeid(optional)
- Select
- Change
- Return to the Set up Single Sign-On with SAML page and download Certificate (Base64) from the “SAML Signing Certificate” section. Edit the
Kimai Cloud.cerfile and copy&paste the content into the Cloud configuration fieldX.509 Certificate. - Copy the values of Set up Kimai-Cloud into the Cloud configuration:
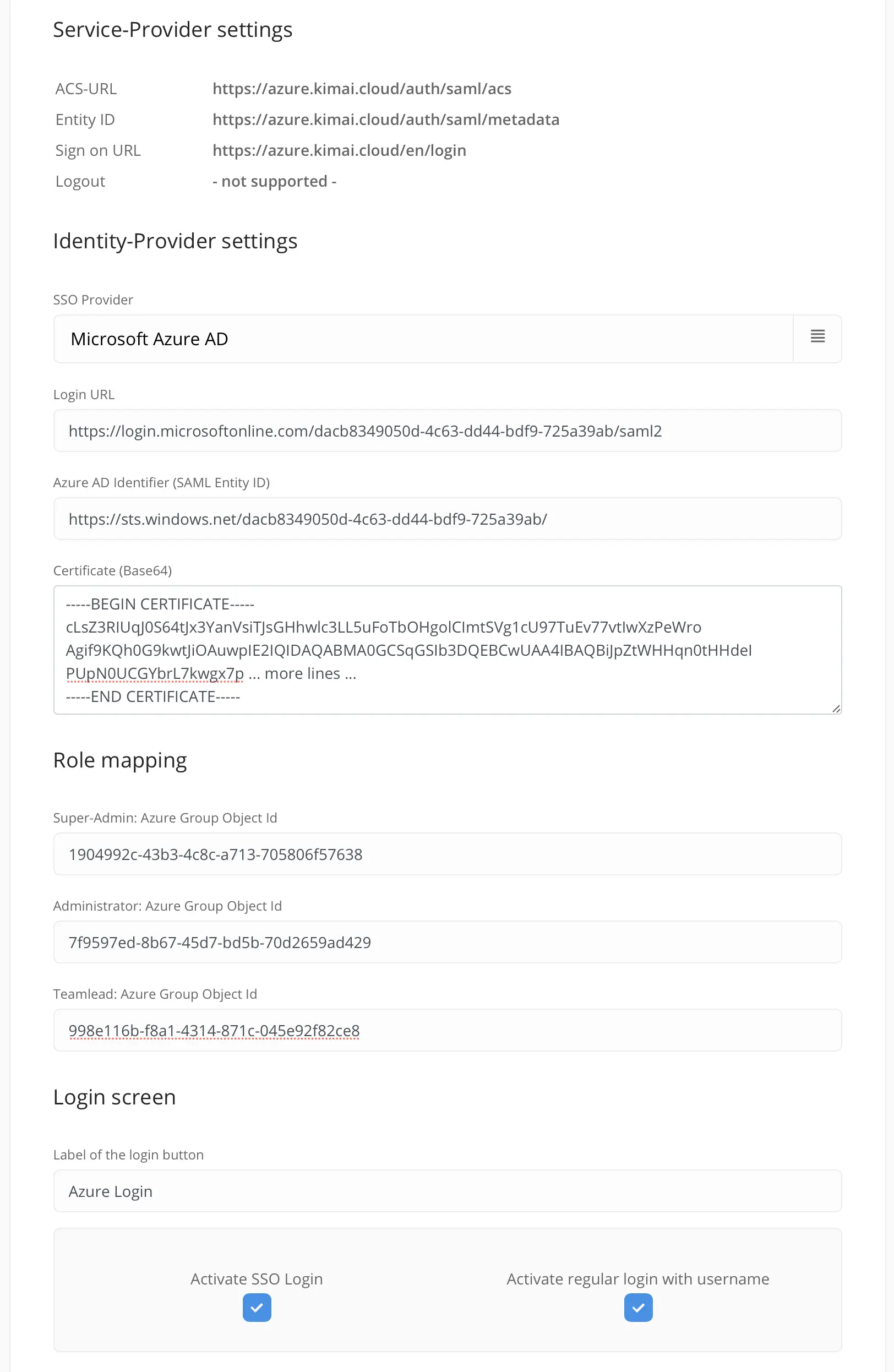
- Login URL:
Login URL - Microsoft Entra Identifier:
Azure AD Identifier (SAML Entity ID)
- Login URL:
Configure “Attributes & Claims”:
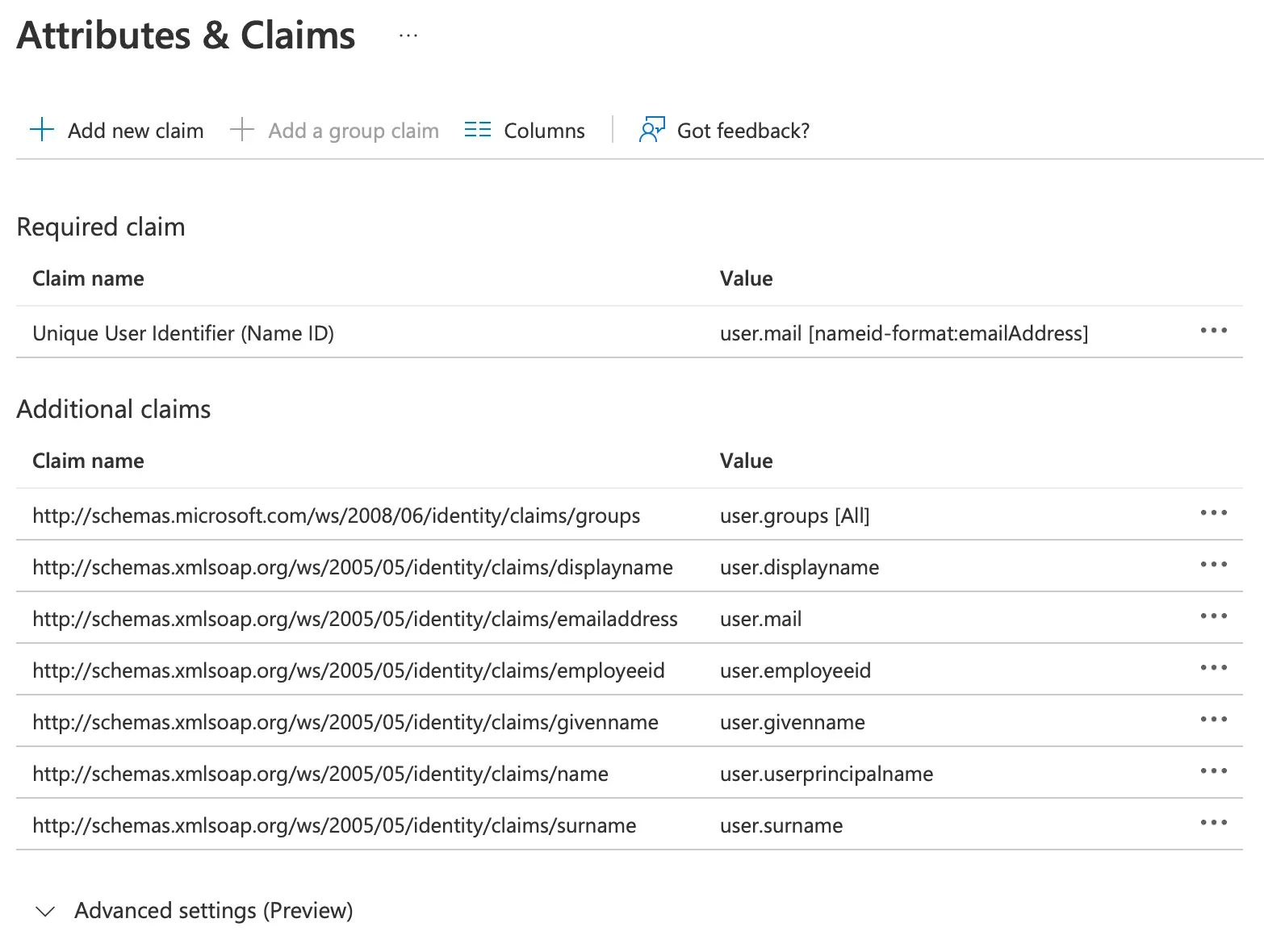
Configure “Groups”:
- In the “Azure Active Directory” section, choose “Groups” from the navigation.
- Click “New group” (with the group type: Security) and repeat this action for each group:
- Set the name
Kimai Teamleadand add members - Set the name
Kimai Adminand add members - Set the name
Kimai System-Adminand add members
- Set the name
- Copy & paste the
Object Idof each group into the Cloud configuration (see screenshot below).
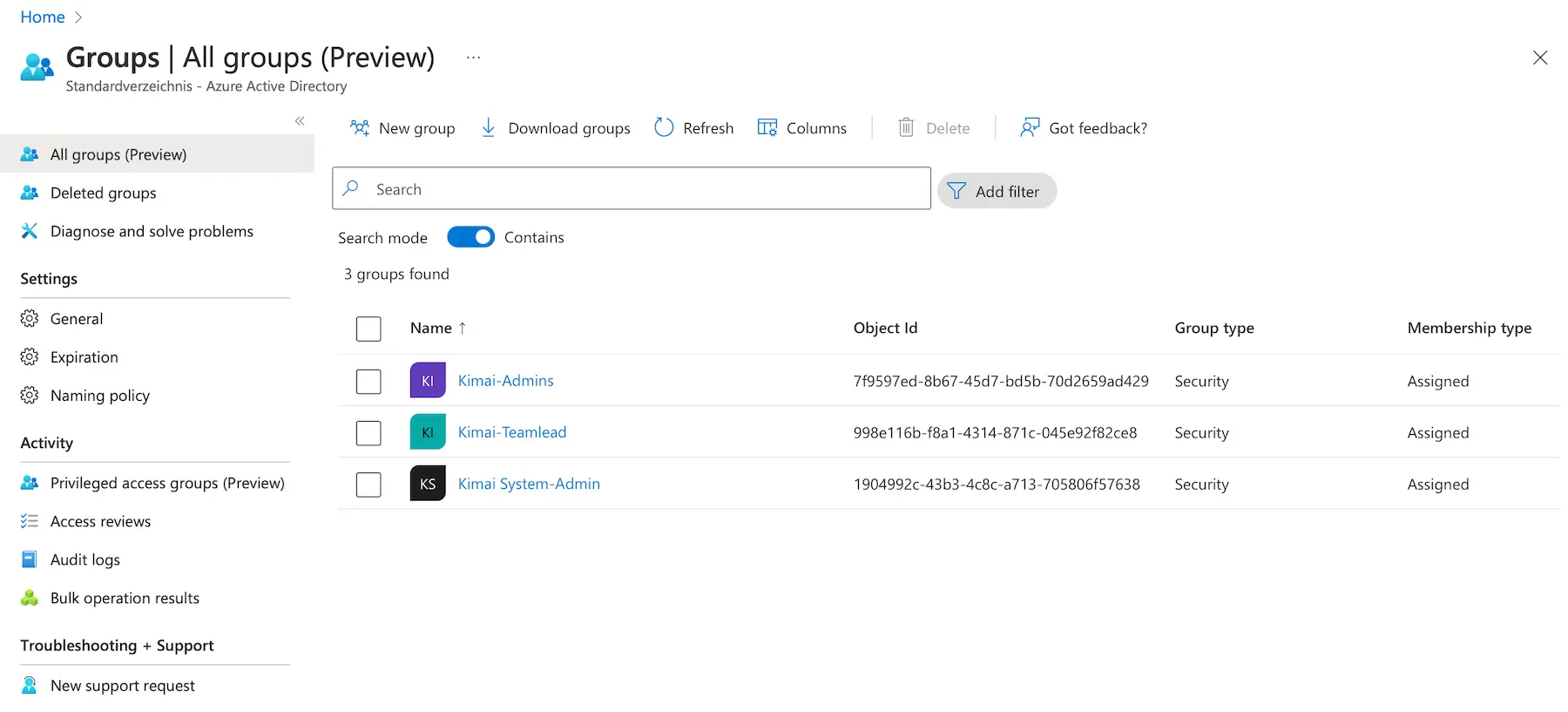
Cloud configuration
Keycloak SAML
Start by setting up your Keycloak following the Keycloak docs.
There is one difference though: the cloud does not activate authnRequestsSigned, which means you have to deactivate Client signature required.
Then make sure to define the User attribute mapping like this (correct case is important, and you need to configure all attributes, even if you do not use them):
Basic Information > Primary email→EmailBasic Information > First name→FirstNameBasic Information > Last name→LastNameEmployee Details > Employee ID→AccountNumberEmployee Details > Title→Title
Important: Edit the SAML capabilities and set the Name ID format to email.